Chaque jour, nous vous offrons des logiciels sous licence GRATUITS que vous devriez autrement payer!

Giveaway of the day — CryptoBuster 1.0.9 Beta 2
L'offre gratuite du jour pour CryptoBuster 1.0.9 Beta 2 était valable le 30 mai 2022!
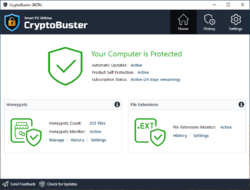
CryptoBuster is an effective anti-ransomware solution with a small system footprint that can work side by side with your existing security product to offer an additional security layer and form the last line of defense against ransomware to protect your valuable data from damage.
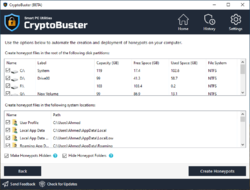
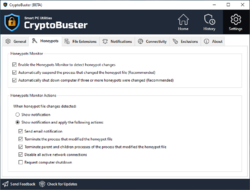
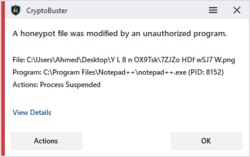
CryptoBuster uses honeypots, which is an efficient and proven technique with low false-positive chances to detect and stop ransomware when they start to encrypt user files. You have full control over the honeypots creation process as you can either create honeypots manually customizing their names and locations or you can leave this job to CryptoBuster that can deploy hundreds of honeypots in strategic system locations with custom names and file types designed to allow ransomware to target those files before they can reach any of your important files.
Besides Honeypots that are effective to stop ransomware when they start to encrypt user files, CryptoBuster can intelligently monitor the file system to detect malicious activities that may indicate an ongoing ransomware attack or sometimes indicate the preparations for an attack. For example, CryptoBuster can detect the creation of files with extensions that are known to be used by ransomware to encrypt user files, also you can configure CryptoBuster to detect the creation of potentially dangerous files like batch files and scripts that are commonly used in ransomware attacks, or even to detect the creation of files of unknown types which is an aggressive technique used to stop most of the ransomware strains that change file extensions.
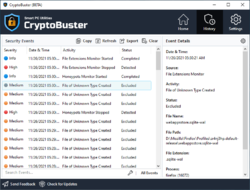
CryptoBuster was built to be a user-friendly and configurable anti-ransomware solution that is why it comes with a full range of tools and settings to allow you to customize all ransomware protection aspects provided by CryptoBuster and to have full control over actions made by the software. You can choose which protection module to enable and configure how this module works, configure automatic actions to perform in response to a specific event or disable this automatic response by setting CryptoBuster to monitor and report only. CryptoBuster comes with Security History feature that logs every security issue detected and actions performed by CryptoBuster; this would allow experienced users to understand how CryptoBuster works and the best way to configure the protection settings for best performance and user experience.
Configuration minimale:
Windows 11/ 10 (32-Bit and 64-bit); Microsoft .NET Framework 4.8
Éditeur:
Smart PC UtilitiesPage web:
https://www.smartpcutilities.com/cryptobuster.htmlTaille du fichier:
12.1 MB
Licence details:
1 year free updates
Prix:
$22.95

Commentaires sur CryptoBuster 1.0.9 Beta 2
Please add a comment explaining the reason behind your vote.
How it works internally I wonder ? From my knowledge ransomware is form of a rootkit, which operates on low level by hooking APIs working with files and encrypting/decrypting doing there - meaning from windows everything looks pretty much normal, until hook is removed - only then encryption is visible, right ?
So this 'buster' is something like 'Unhackme' or similar software hooking itself even somewhere lower (as dangerous as it sounds, makes it pretty much rootkit itself!) or it is just 'monitoring' windows file API activities (as useless as it sounds for finding ransomware) ?
Save | Cancel
dex, Not all ransomware are rootkits; most of them run in the User Mode which makes all their malicious and encryption activity visible to the OS and other apps. The current CryptoBuster Beta can only monitor and respond to IO activities made to honeypots or other file types monitored by the File Extensions Monitor. When a malicious IO activity is detected, CryptoBuster will respond with a variety of actions configured by the user. Those actions aim to halt the ransomware encryption activity, thus minimizing the damage.
Please be informed that CryptoBuster is designed to work with other security apps, so it can't offer full protection against ransomware by itself.
We are working on a file system driver for CryptoBuster that will not only allow CryptoBuster to monitor and respond to malicious activities, but it would allow the app to intercept and prevent honeypot modifications and other IO activities at the Kernel level.
Save | Cancel
Once installed, is there a way to test it to see if it actually works?
Save | Cancel
Port 139 is utilized by NetBIOS Session service. Enabling NetBIOS services provide access to shared resources like files and printers not only to your network computers but also to anyone across the internet. Therefore it is advisable to block port 139 in the Firewall.
Save | Cancel
After installing
Unable to communicate with the Cryptobuster service
What should I do ???
Save | Cancel
Block ports 139 (NetBIOS), 445 (Server Message Block), and 3389 (Terminal Services). These are the ports that APT29 uses. APT29 is the Russian hacking group that is causing much of the ransomware attacks. You're wise if you block these ports on your machine(s).
Save | Cancel